What do you use to check the security of your wordpress?
As everyone knows, WordPress is the leader of CMS, which is why it is also the most constantly attacked for vulnerabilities. There are many security plugins to prevent your website from being compromised, there are plugins of all kinds, from free, free that have all its features but with a delay of 30 days in the main features and free up to date but with basic functionality in addition to the premium. If you do not have to invest in premium plugins I recommend the free one with basic features rather than a complete one with 30 days delay, because 30 days is a long time.
But have you ever tried how secure is your WordPress? For this there are many ways, today we bring you WPScan a very simple way for everyone with a database of vulnerabilities with constant updates and an API that will allow us 50 requests per day for free.
It also has a plugin for wordpress which we will not talk about but you can try, where the free version also allows 50 API requests per day with monthly notification by mail if it detects any, which as I say find out days after …. you can see the plans on their website.
Here we are going to see how to launch it from our machine, for this we have installed a WordPress with a vulnerability due to the Contact Form 7 plugin, which we will scan with this tool after installation.
The first thing is to install ruby since it is programmed in ruby.
sudo apt install ruby
Now the dependencies
sudo apt install build-essential libcurl4-openssl-dev libxml2 libxml2-dev libxslt1-dev ruby-dev libgmp-dev zlib1g-dev
And finally the tool
sudo gem install wpscan
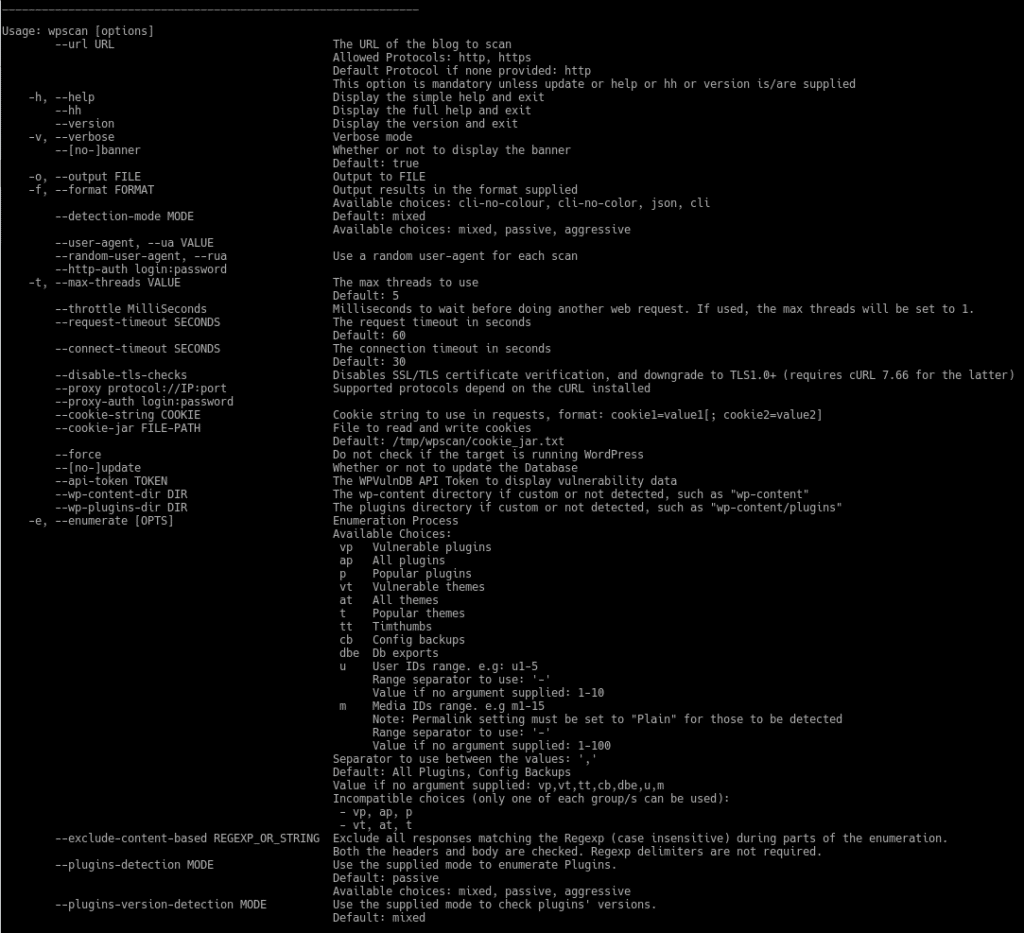
The installation is very simple. Once installed we will see the help by typing
wpscan –hh
We already have the tool installed, now we will check our WordPress with vulnerability in Contact Form 7. In order to use the API you need to register at wpvulndb.com , where I recommend you also activate the checkbox “Receive a monthly digest for new vulnerabilities” to be up to date, we usually receive a few mails during the month.
Ok, we are supposed to have registered and have the API token, let’s use the following basic command
wpscan –url http://webwewanttoscan.com –api-token followedbyyourtoken
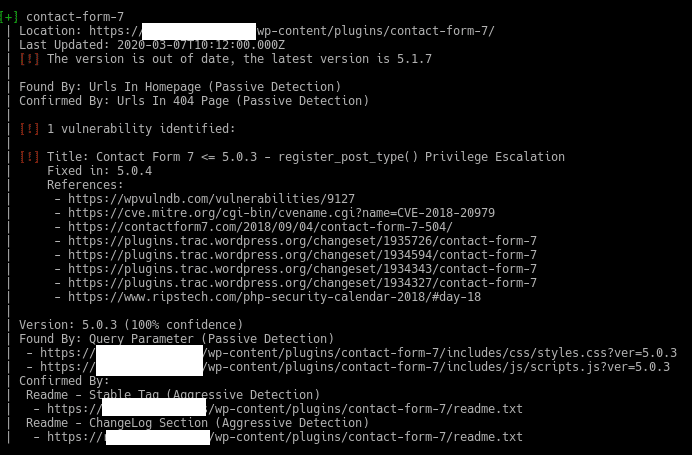
And it will return us the vulnerabilities that have been in the different plugins by versions and which is the one that we have, in our case we have put the 5.0.3 of Contact Form 7 on purpose.
As we can see it tells us that the plugin is outdated and that we have version 5.0.3 with a privilege escalation vulnerability and its references.
If you take a look at the help you can see what else we can do, such as enumerate users, theme, plugins, the type of detection mixed,passive,aggressive, activate the verbose mode and even test brute force attacks with dictionaries.
Some example:
- Scan vulnerable plugins in aggressive mode with verbose enabled.
wpscan –url https://webwewanttoscan.com –enumerate vp –detection-mode aggressive -v
- Brute force testing using a dictionary and 20 simultaneous threads for user wpadmin
wpscan –url https://webwewanttoscan.com –wordlist dictionaries.lst –username wpadmin –threads 20
- List users
wpscan –url https://webwewanttoscan.com –enumerate u
You can spend some time testing things with this tool.
Remember that karma is not confined by covid-19.
TL.