ZEXTRAS CARBONIO COMMUNITY EDITION, YOUR DATA, YOUR CONTROL
We live in a world where data is everything. From our work conversations to the most important documents of a project, everything is digitalized, stored and, many times, shared without us really knowing what happens to that information. Who has control over our data? If we stop to think about it, all our information and that of many companies is in services managed by third parties that are not under our direct control. Therefore, we do not know what happens to that information, nor where in the world it is stored or of course who has access to it. That is why many companies are concerned and look for secure alternatives that do not compromise their data or generate technological dependencies and Zextras Carbonio is a good alternative. What can you do with Zextras Carbonio Community Edition? The answer is simple: practically everything you need to work and collaborate.- Professional email: Manage your communications efficiently with a modern and adaptable tool.
- Secure chat and video calls:Forget about depending on platforms that don’t guarantee privacy.
- Collaboration on documents: Work with your team in real time, without sacrificing control of your files.
- Centralized storage: Keep all your files in a safe place, accessible only to people you authorize.
Rol MTA (Mail Transfer Agent):
-
- 25/TCP (SMTP): Receiving incoming emails between servers.
- 465/TCP (SMTP sobre TLS): Sending emails with TLS.
- 587/TCP (SMTP autenticado): Sending authenticated emails requires STARTTLS.
Rol Proxy:
-
- 80/TCP (HTTP): Unsecured connection to Carbonio web client, redirected to https.
- 110/TCP (POP3): External POP3 services.
- 143/TCP (IMAP): External IMAP services.
- 443/TCP (HTTPS): Secure connection to the Carbonio web client.
- 993/TCP (IMAPS): External secure IMAP access.
- 995/TCP (POP3S): External secure POP3 access.
- 5222/TCP (XMPP): Required by the Work Stream Collaboration (Chat) role.
- 6071/TCP (HTTPS): Secure access to the Administration Panel.
Rol Carbonio VideoServer:
-
- 20000-40000/UDP: Client connections for audio and video transmissions.
En cada Nodo:
-
- 22/TCP (SSH): SSH access for administration.
- 8301/TCP y UDP: Managing the Gossip protocol on the LAN.
- 9100/TCP: Data exporter for Carbonio Monitoring Node.
- 9256/TCP: Process exporter for Carbonio Monitoring.
Rol Postgres:
-
- 5432/TCP: Access to the Postgres database.
- 9187/TCP: Exporting data from Postgres for Carbonio Monitoring.
Rol Directory Server:
-
- 389/TCP: Insecure LDAP connection.
- 636/TCP: Secure LDAP connection.
- 9330/TCP: Exporting LDAP data for Carbonio Monitoring.
Rol MTA:
-
- 25/TCP (SMTP): Receiving incoming emails.
- 465/TCP (SMTP sobre TLS): Sending emails with TLS.
- 587/TCP (SMTP autenticado): Sending authenticated emails requires STARTTLS.
- 7026/TCP: Milter service link address.
Rol Mailstore & Provisioning:
-
- 7025/TCP: Local mail exchange using the LMTP protocol.
- 7071/TCP: SOAP services communication.
- 7072/TCP: NGINX Discovery and Authentication.
- 7073/TCP: SASL Discovery and Authentication.
- 7110/TCP: Internal POP3 services.
- 7143/TCP: Internal IMAP services.
- 7993/TCP: Internal secure IMAP access.
- 7995/TCP: Internal secure POP3 access.
- 8080/TCP: Access to internal HTTP services.
- 8443/TCP: Internal HTTPS services.
- 8735/TCP: Internal mailbox communication.
- 8742/TCP: Internal HTTP Services, Advanced Module.
- 8743/TCP: Internal HTTPS services, advanced module.
Rol Carbonio VideoServer:
-
- 8090/TCP: Servlet communication.
- 8188/TCP: Internal connection.
Rol Proxy:
-
- 9113/TCP: Exporting nginx data for Carbonio Monitoring.
- 11211/TCP: Access to memcached.
Rol Carbonio Mesh:
-
- 8300/TCP: Managing incoming requests from other agents.
- 8302/TCP y UDP: Gossip protocol management on the WAN.
- 9107/TCP: Exporting data from Carbonio Mesh to Carbonio Monitoring.
- 21000-21255/TCP: Range for sidecar service registration ports (automatically assigned).
proxy1.domain.com is the (first) proxy node
mta1.domain.com is the (first) MTA node
If we expand these roles the following would be:proxy2.domain.com becomes the second proxy node
mta2.domain.com becomes the second MTA node
All of this may seem very complex, but it is not, since once you understand the roles and the manual installation process, it is simple and well documented. You can easily start testing the system with everything on a single node by installing it using the script provided by Zextras. To do this, you only need Ubuntu 22.04 and run these commands to add the Carbonio repositories.sh -c ‘echo “deb [arch=amd64 signed-by=/usr/share/keyrings/zextras.gpg] https://repo.zextras.io/release/ubuntu jammy main” > /etc/apt/sources.list.d/zextras.list’
wget -O- “https://keyserver.ubuntu.com/pks/lookup?op=get&search=0x5dc7680bc4378c471a7fa80f52fd40243e584a21” \ | gpg –dearmor | sudo tee \ /usr/share/keyrings/zextras.gpg > /dev/null
chmod 644 /usr/share/keyrings/zextras.gpg
sh -c ‘echo “deb https://apt.postgresql.org/pub/repos/apt $(lsb_release -cs)-pgdg main” > /etc/apt/sources.list.d/pgdg.list’
wget -O- “https://www.postgresql.org/media/keys/ACCC4CF8.asc” | \ gpg –dearmor | sudo tee /usr/share/keyrings/postgres.gpg > \ /dev/null
chmod 644 /usr/share/keyrings/postgres.gpg sed -i ‘s/deb/deb [signed-by=\/usr\/share\/keyrings\/postgres.gpg] /’ /etc/apt/sources.list.d/pgdg.list
apt-get update
Once we have the repositories, we download the script that you can obtain by visiting their website at Zextras Carbonio Community Edition It is very important that before launching the script our hostname and hosts file have the full name with the domain, otherwise we will receive the error “service-discover: error: invalid binding address selected”, also producing the following errors service-discover: error: unable to open /etc/zextras/service-discover/cluster-credentials.tar.gpg. To do this we launch according to our data or edit both files by hand:hostnamectl set-hostname mail.domain.com
echo -e “127.0.0.1 localhost\n192.168.1.79 mail.domain.com mail” > /etc/hosts
In our case, for testing purposes, it is mail.local, but you must have, for example, mail.domain.com.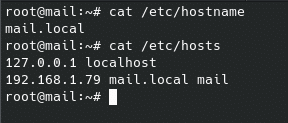
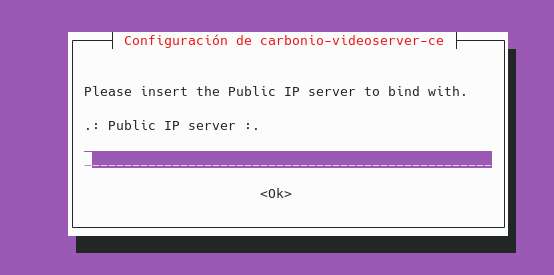
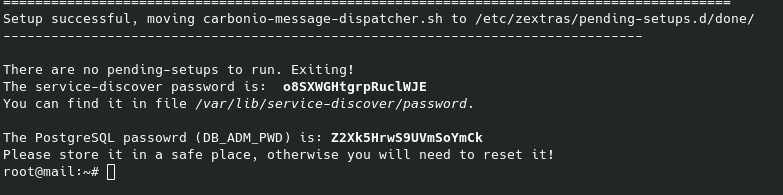
su – zextras -c “carbonio prov setpassword zextras@domain.com tunuevopassword”
If you do it in a test environment like ours where our domain is only local, the user will be zextras@local, that is, only the domain part Once this is done, we can access the administration panel through port 6071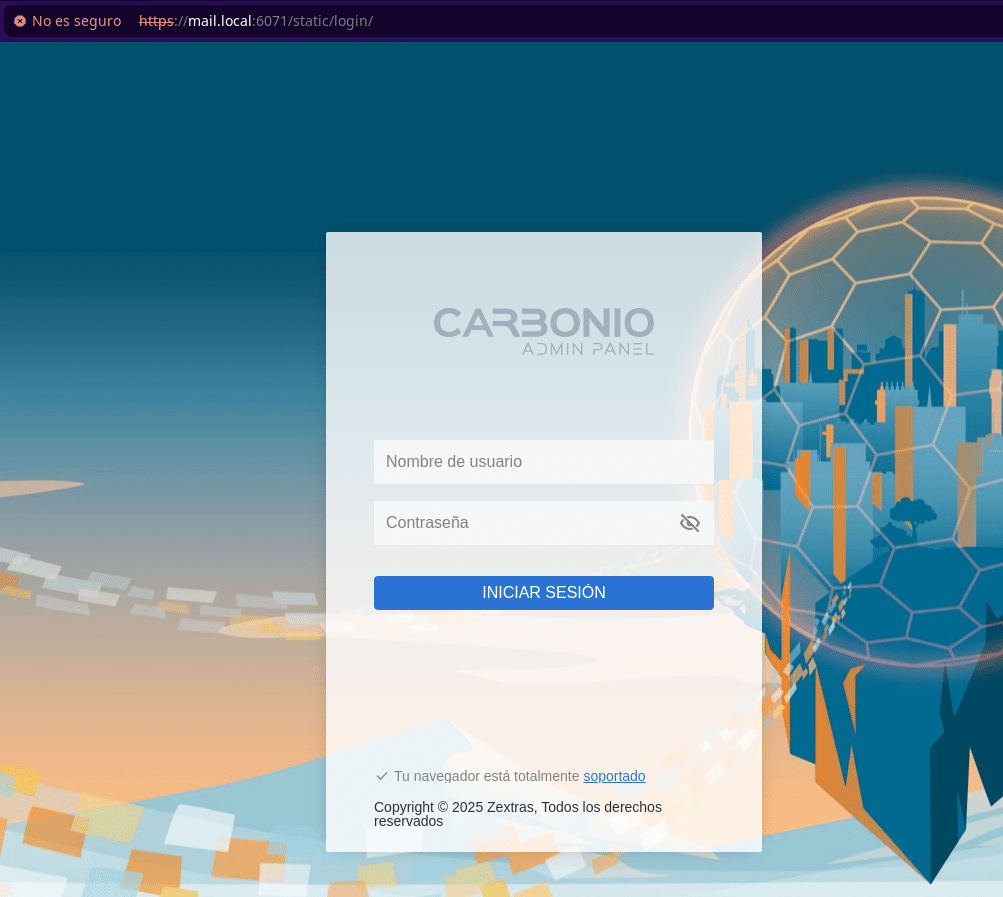

FAQS
Zextras Carbonio CE is an open source collaboration platform that provides security, email, file management, chat and productivity tools for businesses and organizations.
The Community Edition is free and open source, but lacks official support and some advanced features that are available in the Enterprise Edition.
Server with at least 4vCPU, 16GB RAM and 50GB disk. Can be installed on Ubuntu 20.04, Ubuntu 22.04, RHEL8 and RHEL9
Yes, it is a viable alternative for those looking for a secure open source solution without licensing costs, although it requires technical knowledge for its configuration and maintenance.