OPENVAS – Where to start
Openvas is a powerful vulnerability assessment tool that has its Community version. It can be obtained by installing it through repositories, from the source code or by downloading an ISO to install in a virtual machine.
For this post we are going to download the ISO and see its installation. The latest version is currently 6.0.10, you can download it at:
https://files.greenbone.net/download/VM/gsm-ce-6.0.10.iso
Once downloaded the ISO we create our virtual machine in the hypervisor that we like, where minimum we would put 2 vcp, 4 GB RAM and 18GB HD which is recommended and we start from the ISO. Depending on the hypervisor take a look at:
https://docs.greenbone.net/
In the case of VirtualBox tells us to disable audio, floppy and usb, so once the machine is created we edit its configuration and in System we disable the floppy, in Audio we disable the audio and in USB the USB. For the installation it is necessary that the machine has internet. Once this is done, we start the machine from the ISO.
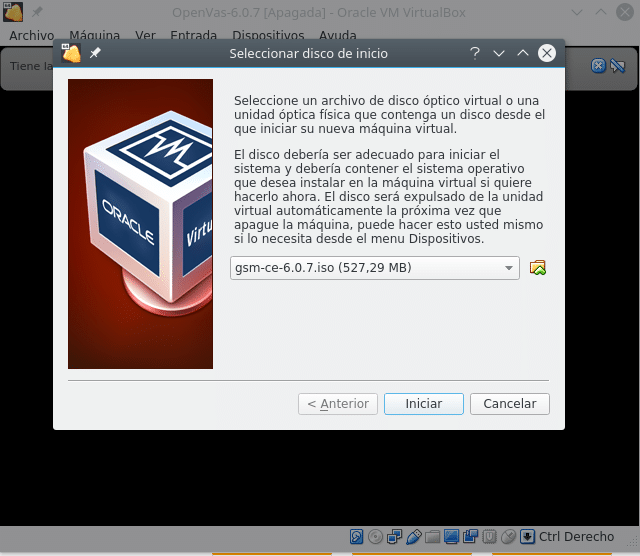
Once the machine has been selected and started, the following menu appears
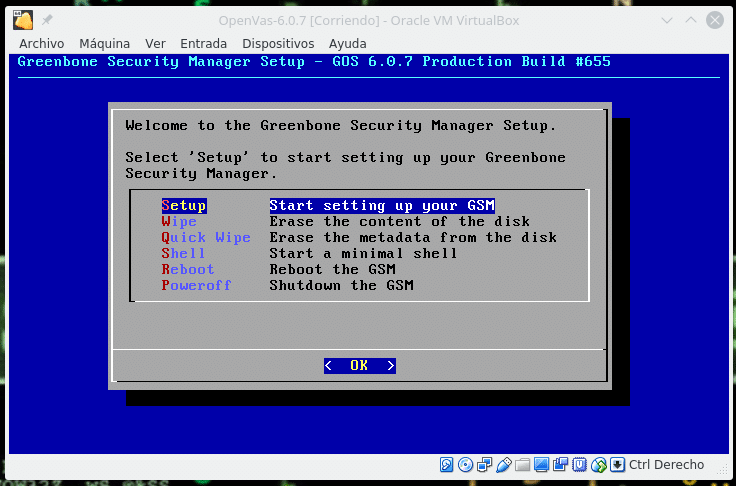
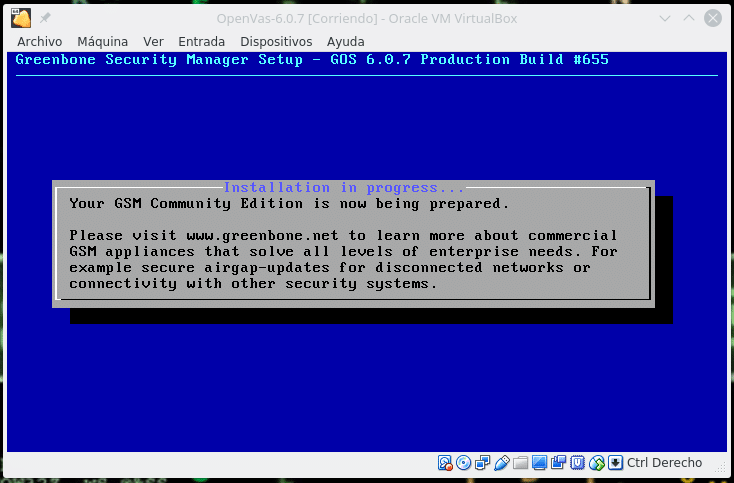
As we are going to install it, we select Setup and it will indicate us that the disk will be formatted and all the data will be erased, we indicate it yes and we continue. During the installation we will see the following screen.
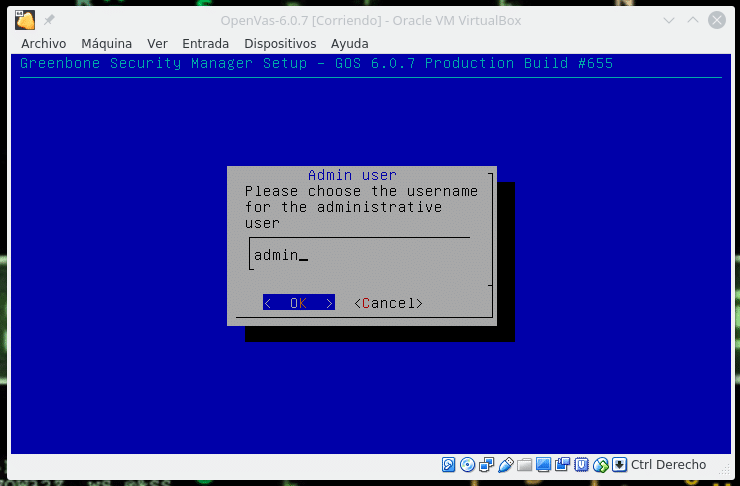
Until you ask for the administrator user
And then the password, we write it and continue, asking to restart, we restart without the ISO, selecting yes in the next screen.
Once restarted it will indicate us that it continues installing and that you do not try to log in, therefore we wait until it restarts again, it is important that the virtual machine has internet.
After a few minutes it will restart and we log in first by shell and the following screen will appear.
We press yes and it will ask us if we want to create a global web administrator, we indicate Yes, we write the user and pass and the next screen will be to upload a subscription, in our case we will skip this step to use only the CE version.
In the next step we will be asked if we want to download the feed, obviously we indicate Yes to feed the Openvas vulnerability database.
This process needs to download a lot of data so it will be slow, if you have any problem, in the menu that will appear go to Setup/Feed/GreenBoneServer/Syncport change the 24 to 443.
We return to the main menu and in Maintenance/Feed we will be able to see
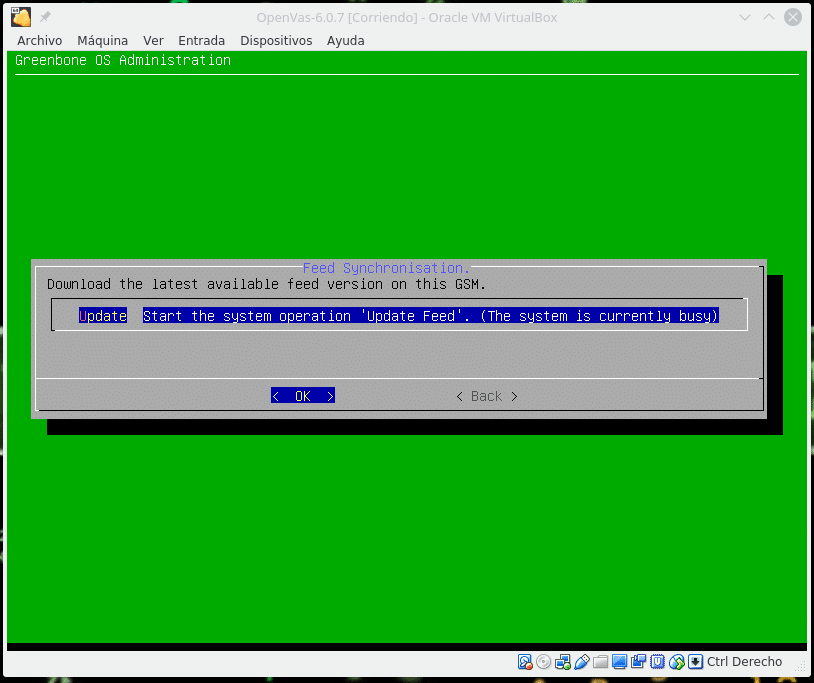
Where we can observe that it is currently busy because it is updating, we take a coffee and come back in a while to see that it has finished. Always before any test that is going to be performed later in time launch an update of the feed.
Once this process is done we access by web to the address of your machine with https, we enter user and pass and we will find the Dashboard
Explaining everything in a single post is a bit complicated so we will explain something basic like scanning a host and interpreting the data. In this link you can find the complete documentation and if you have any doubt I will be happy to help you.
https://docs.greenbone.net
First we click on the user icon at the top right to set the schedule of our server and in General we adjust the parameters
We are going to perform a first scan of a host with default values of our Openvas, in the Scans menu we click on tasks
Where we have the help, the wizard and the option to add a new task.
In this case we are going to click on Advanced Task Wizard
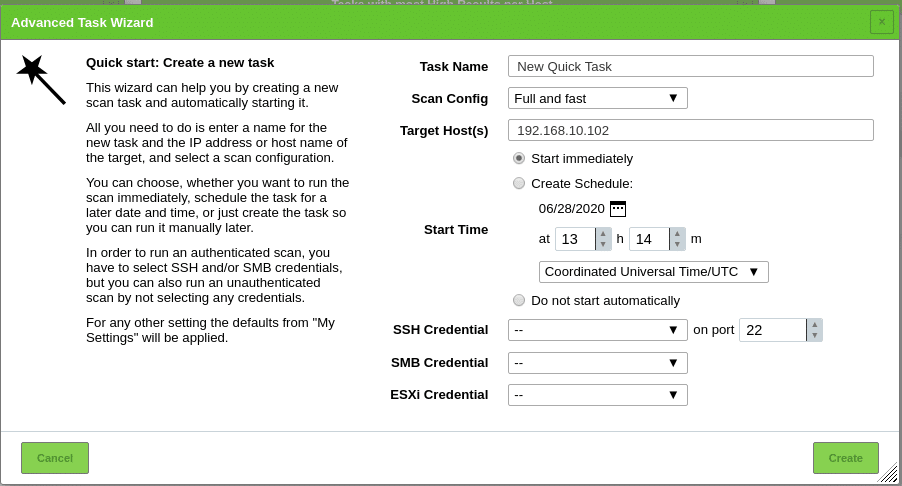
We give it a name, choose the type of scan, the targets, if we want to schedule it and if we want to do it with credentials of the machine to make it more complete.
Here indicate that it is possible that it gives you a failure if you schedule it for the same day or even if you have selected start immediately, in the calendar, select a later date and it will let you create it and start the task.
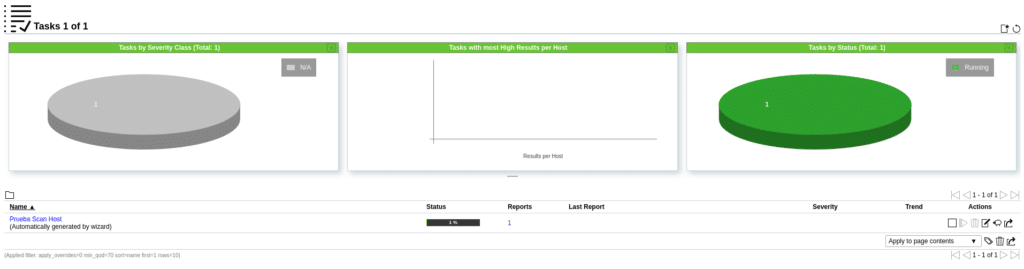
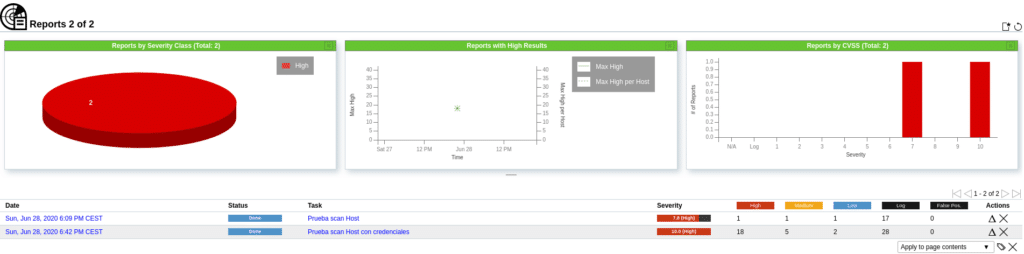
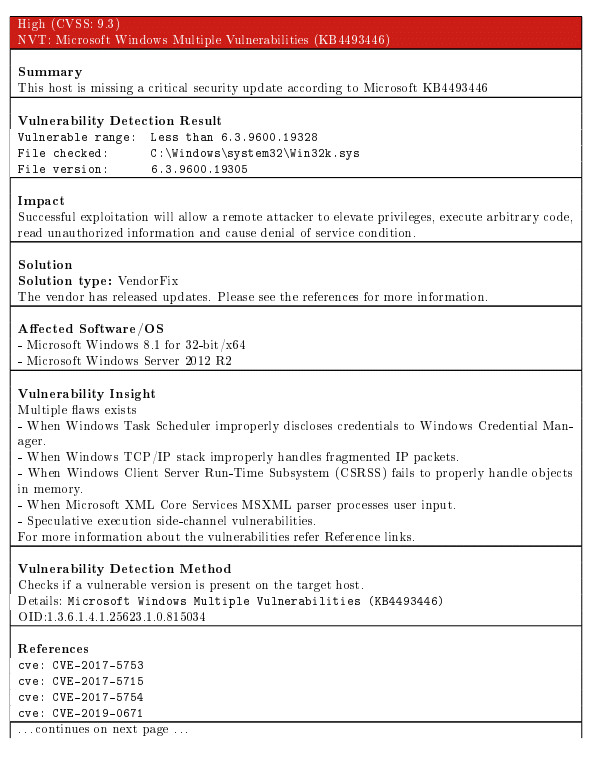
If we click on Reports where it says 1 we will see the process and what is found depending on the type of vulnerability.
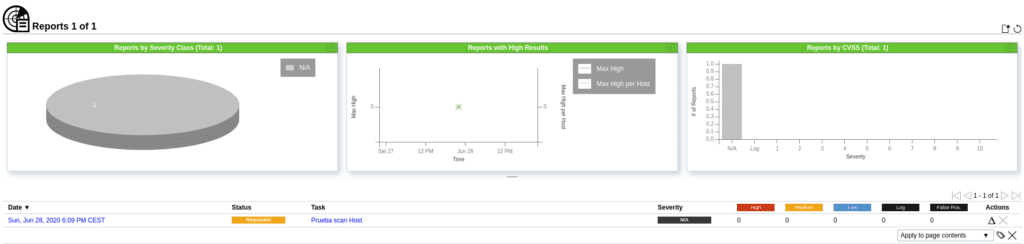
Once the scan is finished, we can see the vulnerabilities found and an average of the risk of that host in Severity, in this case 7.8.
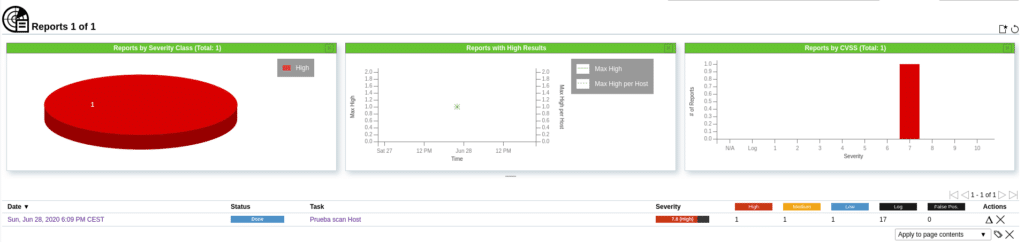
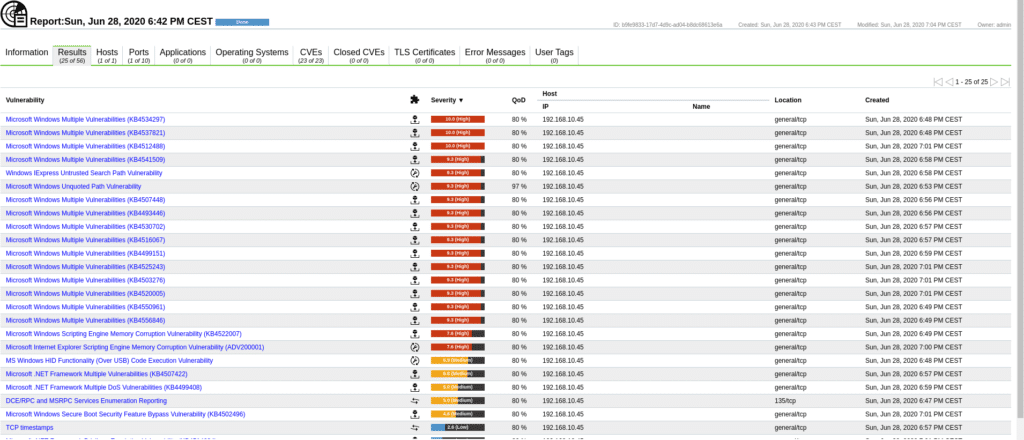
If we click on the report we will obtain the detail sorted as follows.

Clicking on the Results section will show the vulnerabilities
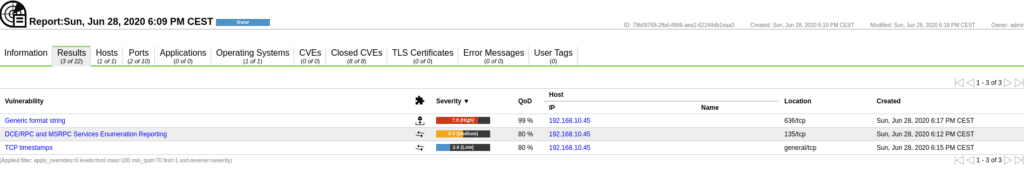
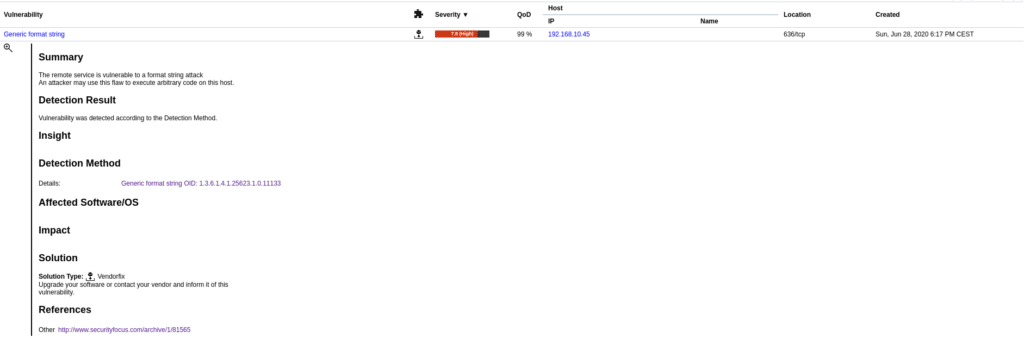
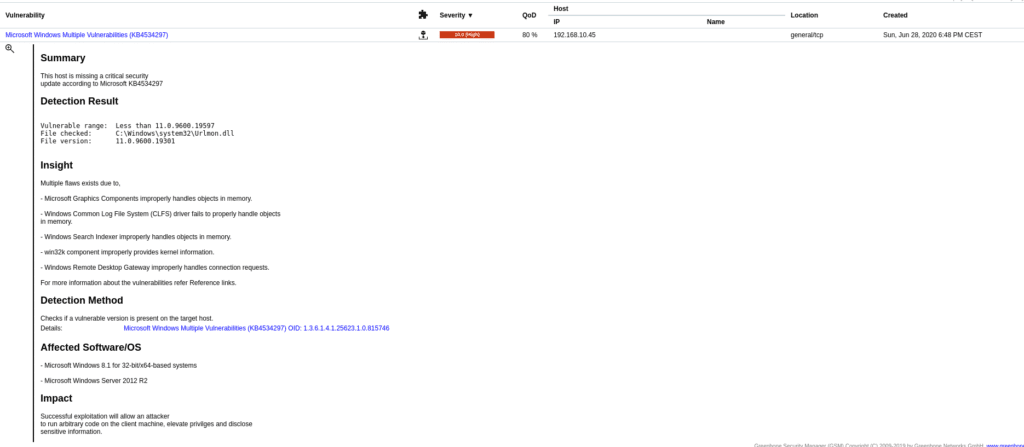
If we open each of them we will see information about it and their solutions or how to reduce the risk.
In the case of the Generic format string vulnerability, the solution is to update the operating system.
In the case of DC/RPC and MSRPC Services Enumeration Reporting, it recommends filtering incoming traffic.

In the other sections we have Hosts, where we get details about the host scanned, Ports the ports detected, Applications applications detected, Operating Systems the operating system, CVEs found, Closed CVEs not vulnerable, in this case being a Windows 2012 it returns us that it is not vulnerable to
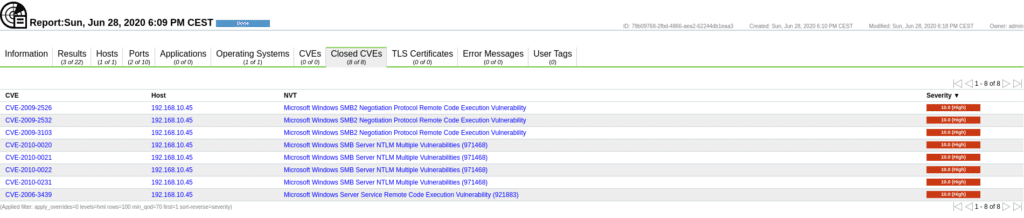
Tls Certificates TLS certificates, Error Messages, error messages during the scan and the user tags that match the ones we have defined in Configuration/Tags.
Now we are going to do the same scan but providing the credentials of the machine in the task. To do this we first go to Configuration/Credentials and add a new one
After adding the credentials in the task wizard we will have them available for selection, in this case being Windows we will select them in SMB Credentials and launch a scan again. As we can see in the following image the number of vulnerabilities is much higher, since I have previously prepared this scenario to protect this machine from many of them by doing an external scan, now I am giving the credentials.
In the upper part of the reports we find the following actions and filters.
These are very useful and we leave it to you to take a look at them. For example the last icon we can export the results in different formats to make any very complete report.

This post is made for educational purposes, do not misuse it, because as I always say do not do what you do not want to be done.
On the other hand, knowing how to handle tools of this type does not imply that you can already do security audits, this is just a grain of sand in a mountain, but if you liked it and you are restless, keep looking and learning new things, there is a universe out there.
TL.







Hola, busca qu te busca cosas en internet sobre el tema, los mil videos, videos hasta de una hora y más, no digo que sean malos, he aprendido mucho con ellos también sobre pfsense, pero hay mil detalles muy bien explicados acá, del pi al pa. Cosas que no están en ninguna parte. Le estoy realmente muy agradecido
Nos alegra que le haya servido nuestros posts. Llevamos tiempo sin poder dedicarle tiempo pero en breves seguiremos publicando nuevos posts.