Easier than it seems
As with any connection made in a Windows environment, the main thing is to use the DNS of your domain. To do this, we configure the network card with said DNS and domain to use in our case PRUEBAS.LOCAL and IP 192.168.10.45
We install NTP and configure it so that our time server is the DC
apt ntp install
nano /etc/ntp.conf
and we replace the pools with our DCs
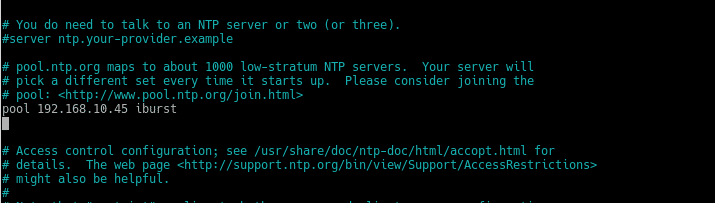
We restart ntp service
service ntp restart
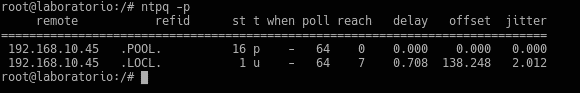
And we verify with ntpq -p that it synchronizes correctly with our DC
Now we proceed to install the necessary packages
apt -y install realmd sssd adcli libwbclient-sssd krb5-user sssd-tools samba-common packagekit samba-common-bin samba-libs
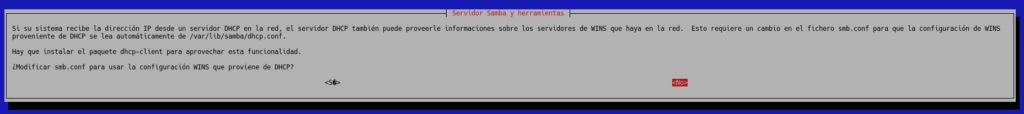
It will ask us if we want to modify smb.conf to use WINS, where we will indicate that No is the default option.
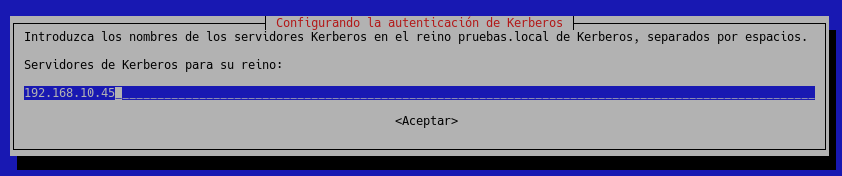
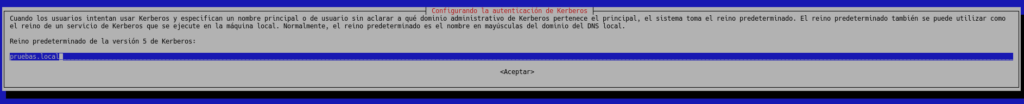
Next, it will ask us for the Kerberos realm where we will put our domain TESTS.LOCAL, in capital letters, although we are going to put it in lowercase so that you can observe the error that will be given if it is not entered in capital letters.
and then the servers in our case 192.168.10.45, its the full name of the FQDN server
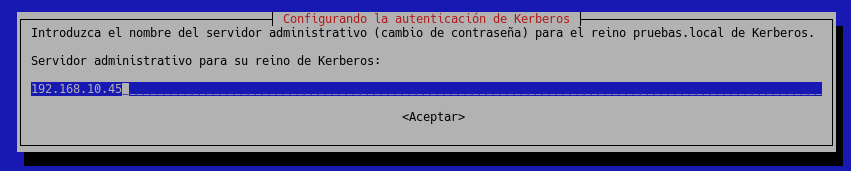
Same for the administrative server
Ok, we already have the main thing installed, be careful in previous versions in some distribution you had to patch the packagekit as in Ubuntu 16.04 from this repository
add-apt-repository ppa:xtrusia/packagekit-fix
apt update
apt upgrade packagekit
Our lab machine, as we saw in a previous post, was upgraded to Debian Buster, we will see at the end if we encounter any problems.
We move on to configure nsswitch, edit /etc/nsswitch.conf and add sss in the following sections, in the case of Debian Buster it does it automatically.
passwd: compat sss
group: compat sss
….
netgroup: nis sss
sudoers: files sss
But it is very important to modify the line
hosts: files mdns4_minimal [NOTFOUND=return] dns
for this other one, where the only thing we do is change the order by putting dns after files, without this change the union will fail.
hosts: files dns mdns4_minimal [NOTFOUND=return]
We create a Kerberos ticket, as follows
kinit -V usarioadministradordominio
BE CAREFUL without the domain name because it will take it from the default_realm which is the one we put in the installation, you will see that it will fail with the message
kinit: KDC reply did not match expectations while getting initial credentials
This is the typical error that happens frequently and we wanted to reproduce it in this post, this is because when it asked us for the realm we put it in lowercase to reproduce this typical error, just edit /etc/krb5.conf and put it in uppercase both in default_realm and in the realms, in addition to adding at the bottom in the section
[domain_realm]
pruebas.local = PRUEBAS.LOCAL
.pruebas.local = PRUEBAS.LOCAL
Of course, with your domain
Once set correctly, we will get
Authenticated to Kerberos v5
Having the ticket we join our machine to the domain, in the OU that we want and with your domain, in our case we have created an OU called Linux Computers
realm join pruebas.local –computer-ou=”ou=Linux Computers,dc=pruebas,dc=local” -U usuarioadministradordominio
and we will get
* Successfully enrolled machine in realm
We already have our machine joined to the domain, now we are going to mount the mobile profiles, for this we first install
apt install smbclient gvfs-fuse gvfs-backends gvfs-bin cifs-utils libpam-mount
Once installed we edit /etc/sssd/sssd.conf
nano /etc/sssd/sssd.conf
and we put the following line in False leaving it like this
use_fully_qualified_names = False
We edit the following
nano /etc/security/pam_mount.conf.xml
and below
<!– Volume definitions –>
We set up the profile by entering the location where we have said user profiles.
<volume user=”*” fstype=”cifs” server=”servidor” path=”/%(USER)” mountpoint=”/home/%(USER)” options=”sec=ntlm,mfsymlinks,nodev,nosuid” />
The entire process of joining the domain and setting up the mobile profile in the user’s /home can be done using scripts, since for example it is very useful when you have a virtual desktop platform, launching said script automatically in the last step of creating the desktop from the broker.
TL.
Thanks for reading our posts.
FAQs
By integrating Linux with Active Directory, administrators can centrally manage users and permissions, enforce security policies, and facilitate access with single credentials (Single Sign-On).
Some useful commands are:
- realm list → To check the domain join status.
- user id@domain.com → To check if the domain user is recognized in the system.
- getent passwd user → To check if the user has an account in the system.
- Authentication failure: Check the system clock with ntpdate to avoid desynchronization with the AD server.
- Name resolution failure: Make sure that /etc/resolv.conf points to the domain’s DNS.
- Unrecognized domain users: Check the sssd.conf configuration and restart the service with systemctl restart sssd.
To verify that Kerberos is working correctly, you can use the command:
kinit user@DOMAIN.COM
If authentication is successful, klist will display the active session ticket.