We finish the Pfsense block with pfBlockerNG
pfBlockerNG is a package that will allow us to block IP addresses based on public lists, countries, domains or own lists, which we can find in pfsense and that together with Suricata we will get a very complete opensource firewall regarding security.
The first thing is to install the package as we have done on other occasions, we go to the System/Package Manager/Available Packages section and look for pfblocker and select install.
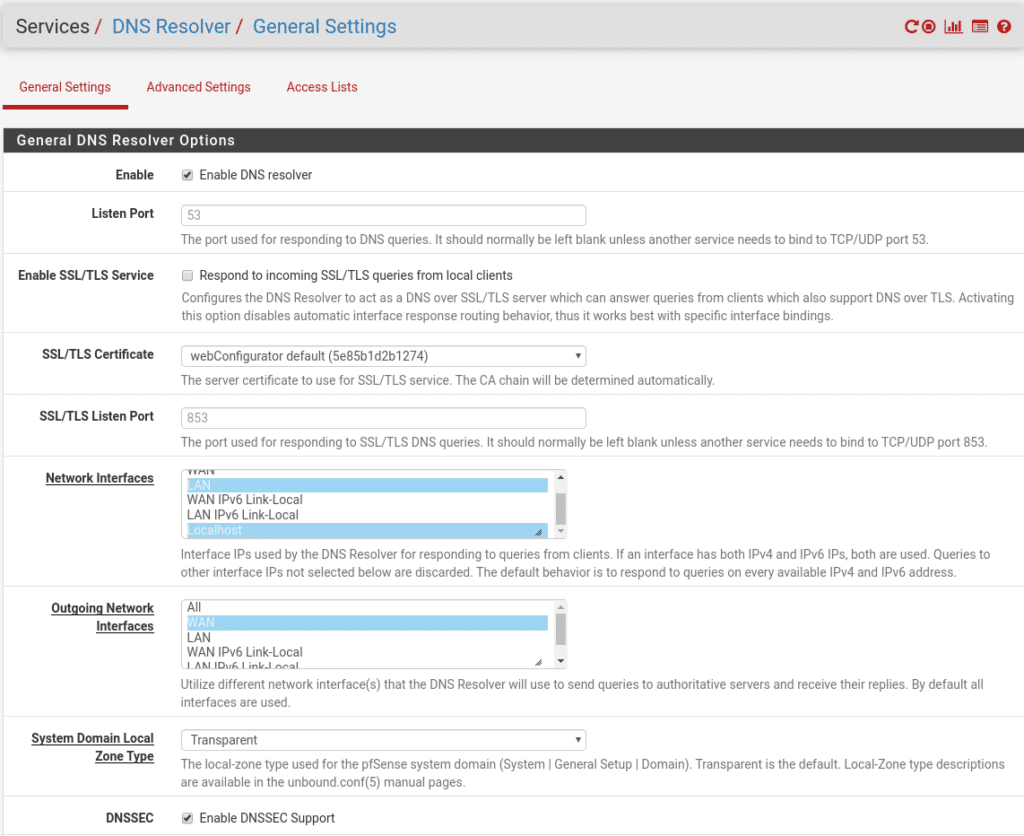
Once installed the first thing to do is to correctly configure the DNS service in Services/DNS Resolver where the important thing is to establish which networks are Wan and which are Lan being in our lab as follows, since by default the pfsense dns service is configured to listen on all interfaces. Maybe we should put this in the first post but supposedly, or so I imagine, nobody would think of putting a firewall in production without having it completely ready.
We give to save applying changes and we begin to configure in the Firewall/pfBlockerNG section.
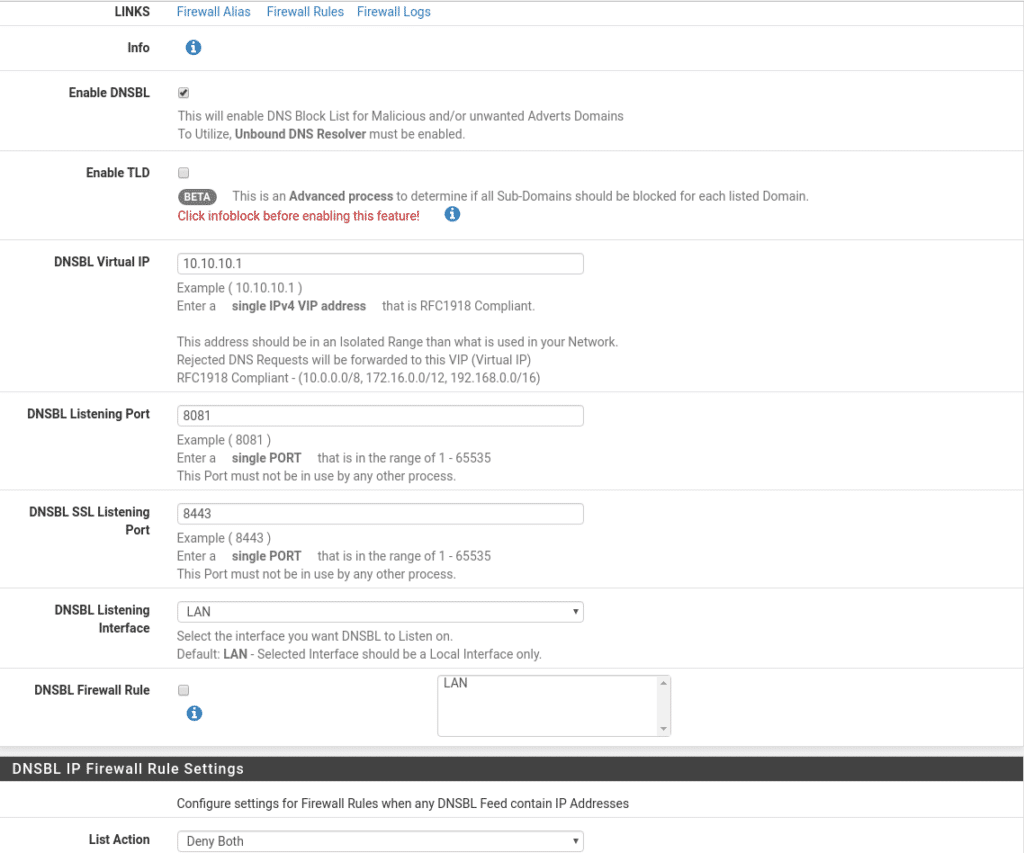
To protect the Lan part and avoid connections to the malicious ips lists the first thing to do is to configure DNSBL which has many options so we will not see all of them, only a basic configuration, where by default it is useful except for the five main points:
- Enable DNSBL – Hehe if we do not activate it, the others are useless.
- DNSBL Virtual IP – In this option we must put a private ip that is not part of any of our private networks where everything rejected will be redirected to be able to monitor and make studies of the behavior in your Lan.
- DNSBL Listening Interface – Select the Lan interface where we want to activate the service.
- DNSBL Firewall Rule – If we have other Lan interfaces we would select this checkbox to automatically open the communication between the other Lan and the service we are configuring, in our case we only have one Lan to protect so it is not necessary to activate it.
- List Action – What action the firewall will perform when there is a connection with any ip of our lists.
Our configuration would look like this.
Once we have this the following 2 options will allow us to protect our Lan based on lists.
DNSBL Feeds allows us to add third party lists, the more lists the more resources we need in our firewall, take it into account. We are going to add the following because they are very good free lists.
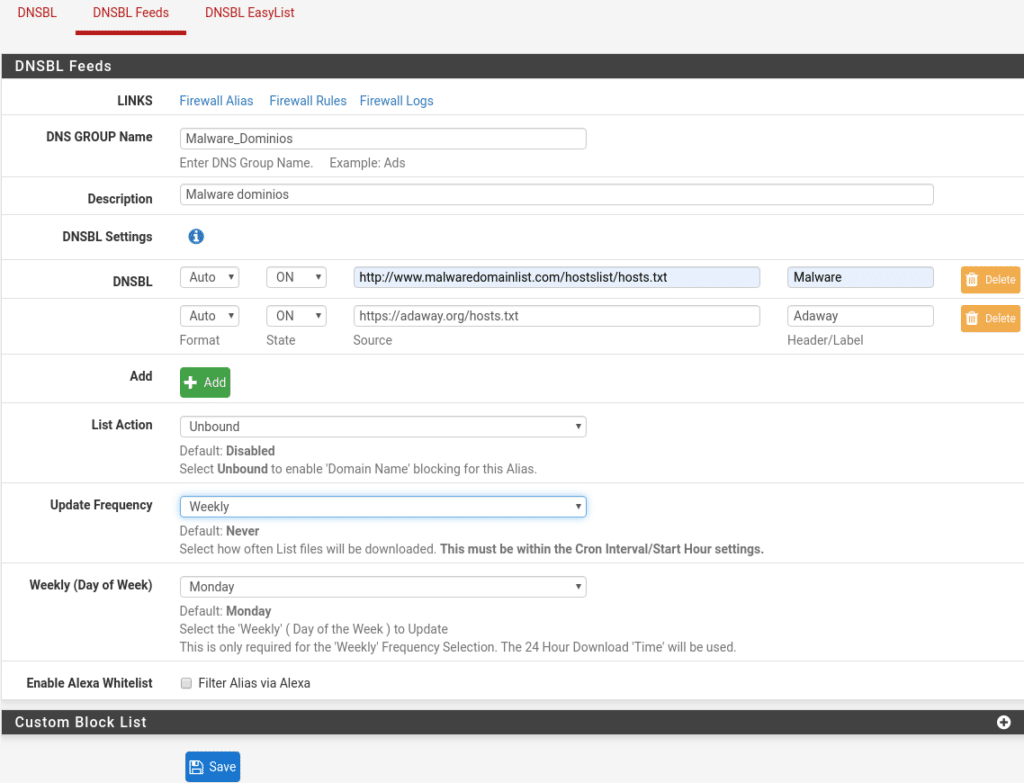
We go to DNSBL Feeds and click on add, we are going to classify them as we want. For example the first classification.
Malware_Domains which we can update once a week for being a little less dangerous and the least updated at source level, spending less resources, with the following lists
https://adaway.org/hosts.txt
Of course you can add the ones you like, create or download.
Do not forget to mark List Action in Unbound.
Now we will create another one that we will update every 6 hours for example being dangerous category with the following lists.
https://www.dshield.org/feeds/suspiciousdomains_High.txt
https://someonewhocares.org/hosts/hosts
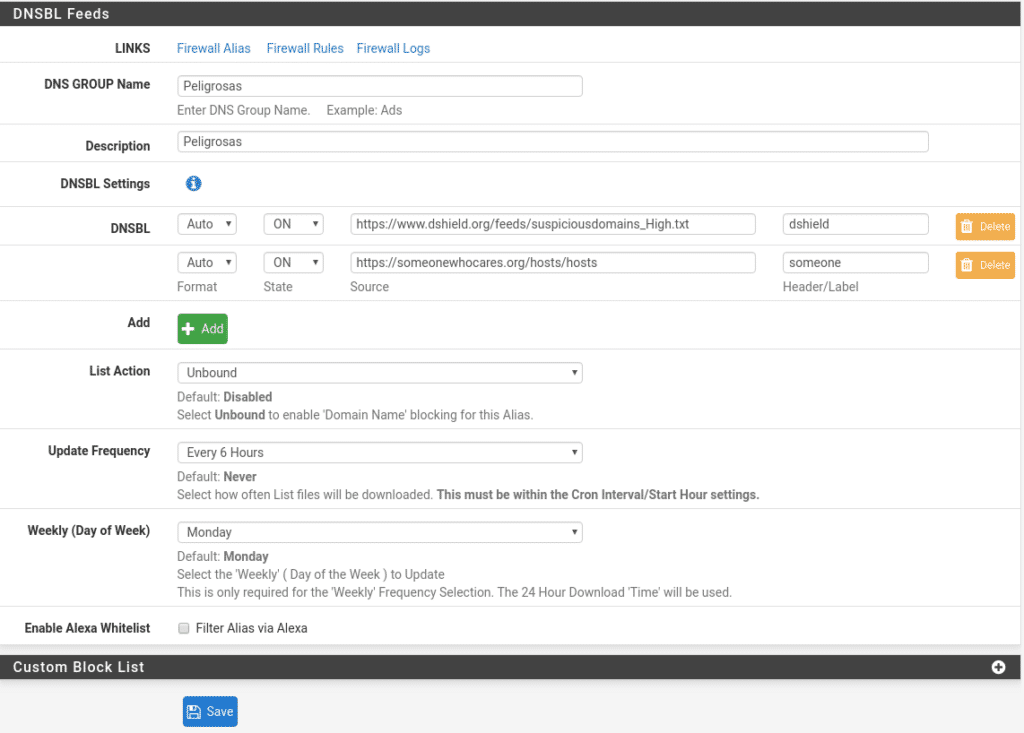
Unfortunately in December 2019 they discontinued the ransomwaretracker lists which were indispensable, to this day we could pass you a copy, but lifeless lists are meaningless.
As for DNSBL EasyList they are lists built into the package itself that we will take advantage of by configuring as follows.
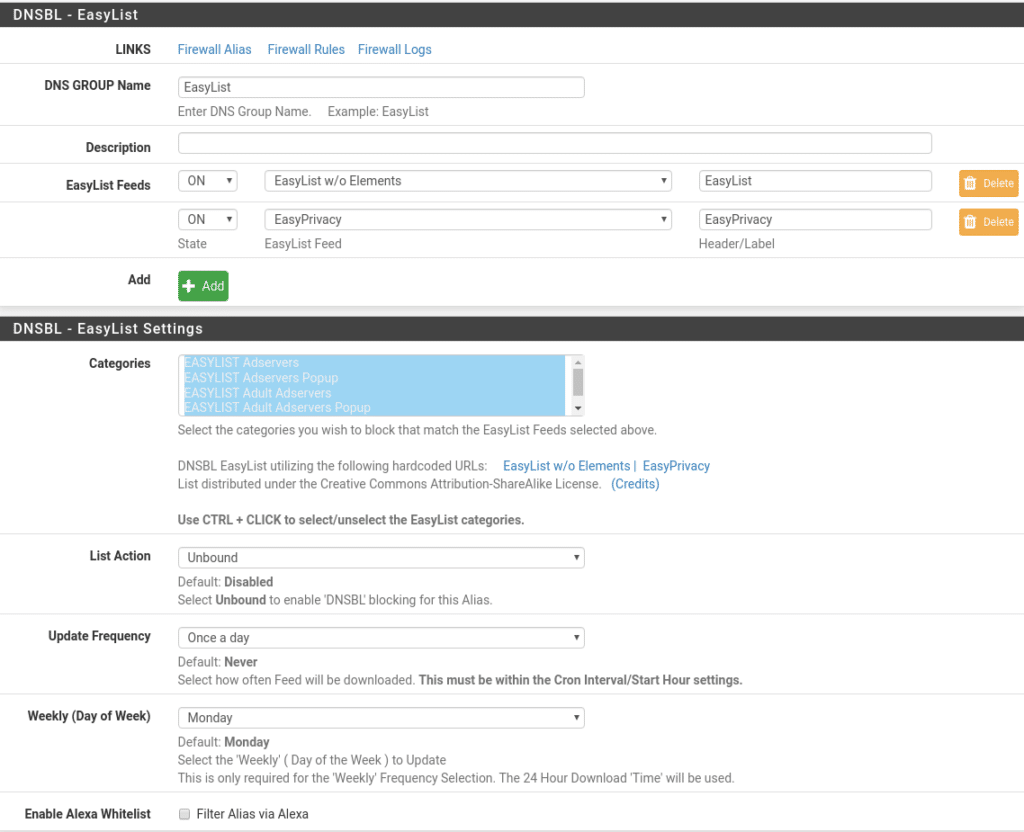
Once this part is done, we will also protect the Wan part, for this we go to Firewall/pfBlockerNG/IPv4 and click on add our first list
Here we are going to classify them in levels, the first one Level-1 with the following lists updating every 2 hours and in both directions. In this list we have to take into account that private networks are included, so if your lab is the same as the one we are dealing with where the Wan of the firewall is in our Lan, you can leave it OFF until the end to avoid being blocked.
https://rules.emergingthreats.net/blockrules/compromised-ips.txt
https://rules.emergingthreats.net/fwrules/emerging-Block-IPs.txt
https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level1.netset
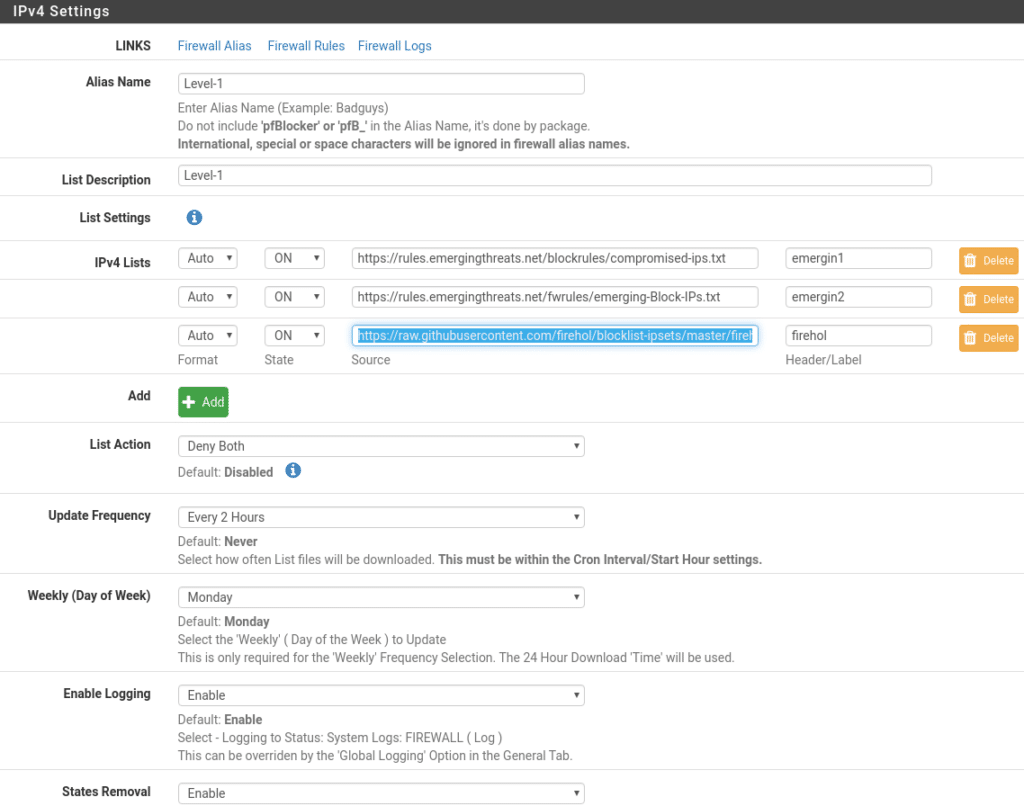
Level-2 with the following lists in both directions every 4 hours
https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level2.netset
https://cinsscore.com/list/ci-badguys.txt
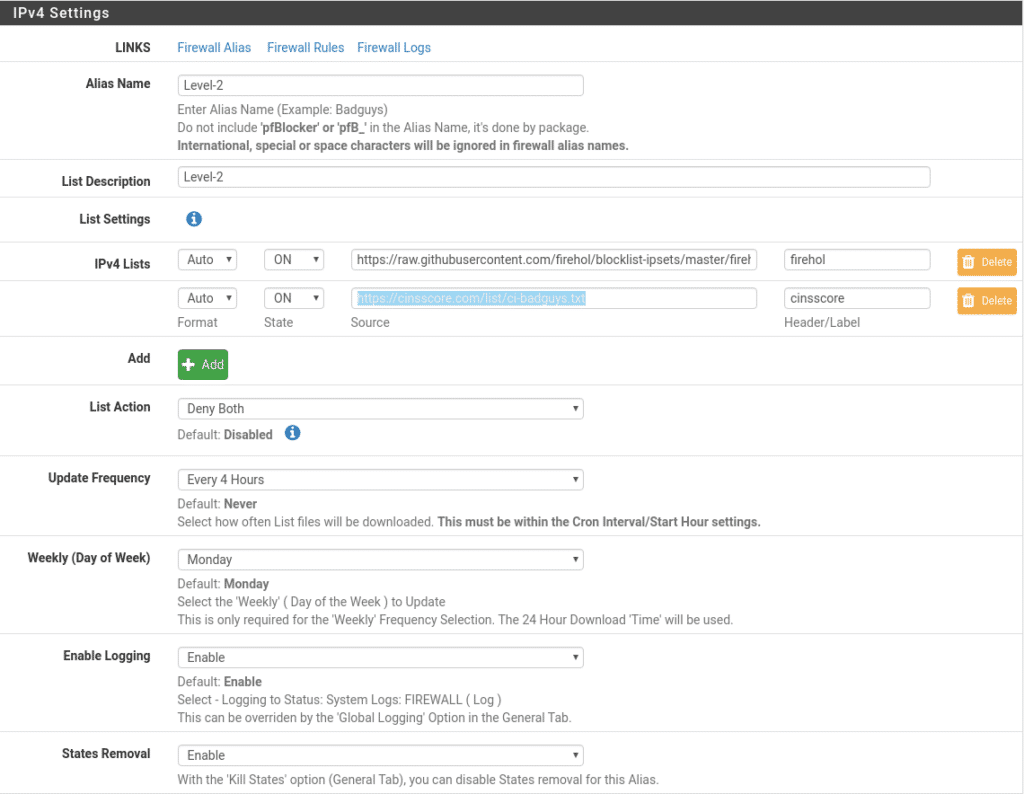
We switch to Level-3 every 8 hours and in both directions.
https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level3.netset
https://lists.blocklist.de/lists/all.txt
http://www.sanyal.org/blocklist.txt o http://sanyalnet-cloud-vps.freeddns.org/blocklist.txt
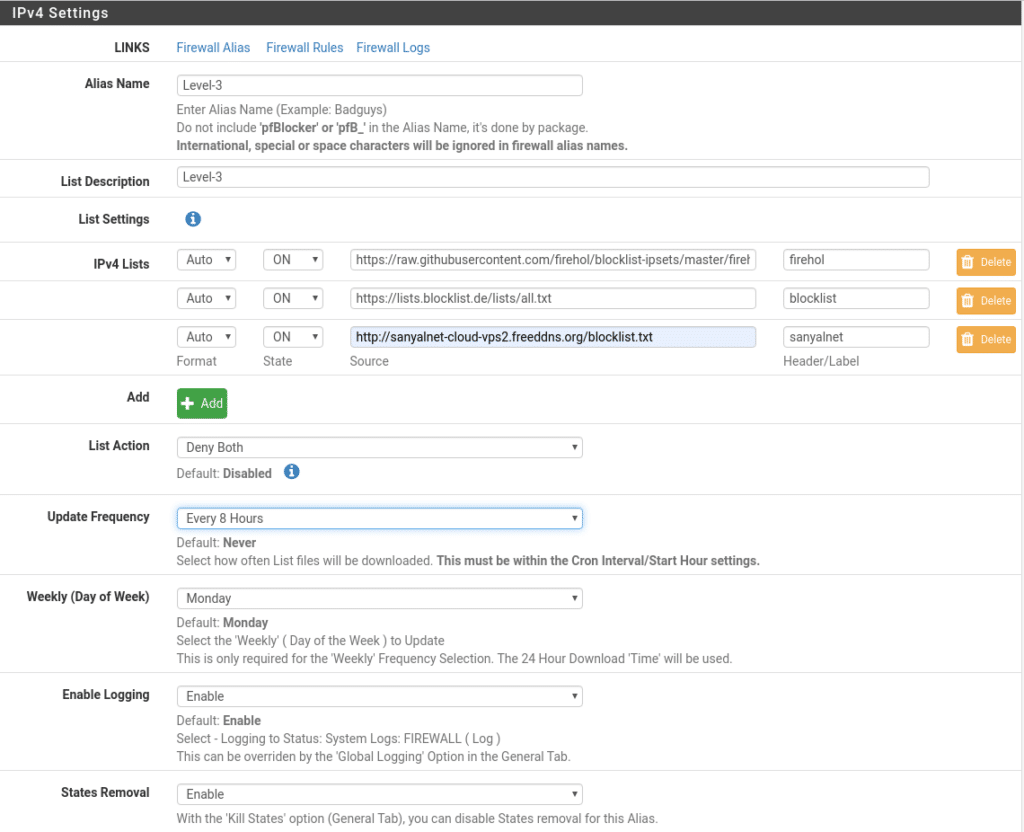
The IPv6 part is exactly the same I leave it to you to look for lists and regarding GeoIP take a look if you want to block countries but first if you have not done it you have to register in MaxMind, the free version is GeoLite2 at this link
https://dev.maxmind.com/geoip/geoip2/geolite2/
Now we just need three little things to activate the service in Firewall/pfBlockerNG and review the parameters to our liking for example if you have changed the language and you use MaxMind select the same language
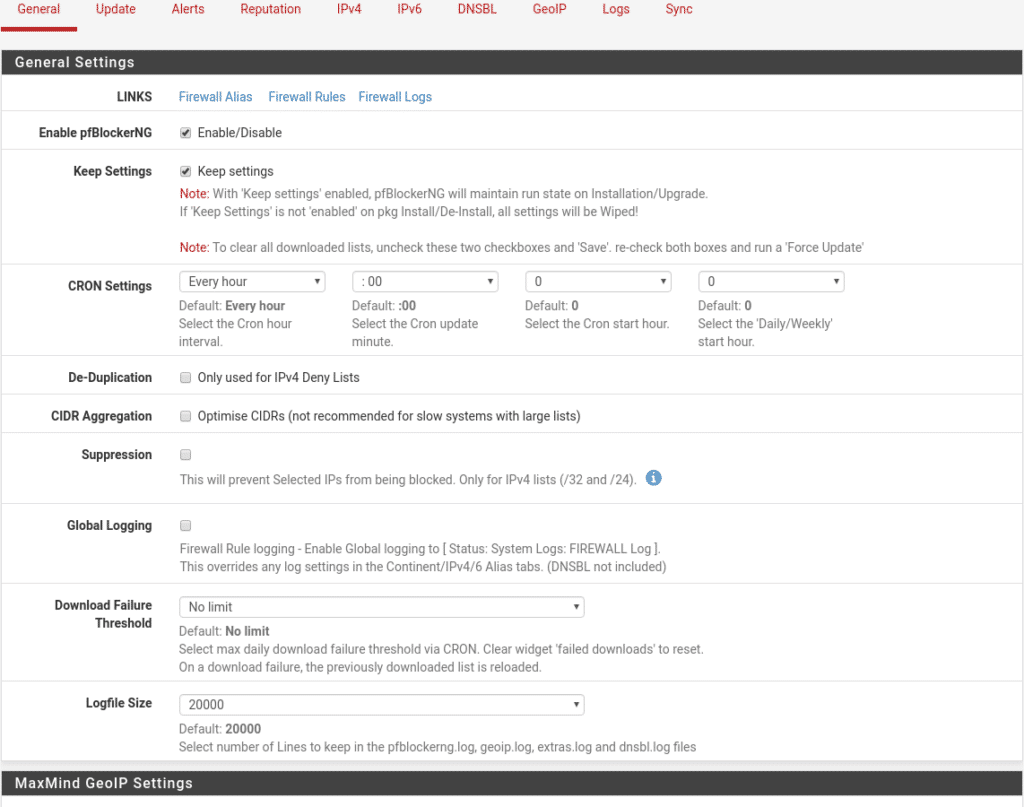
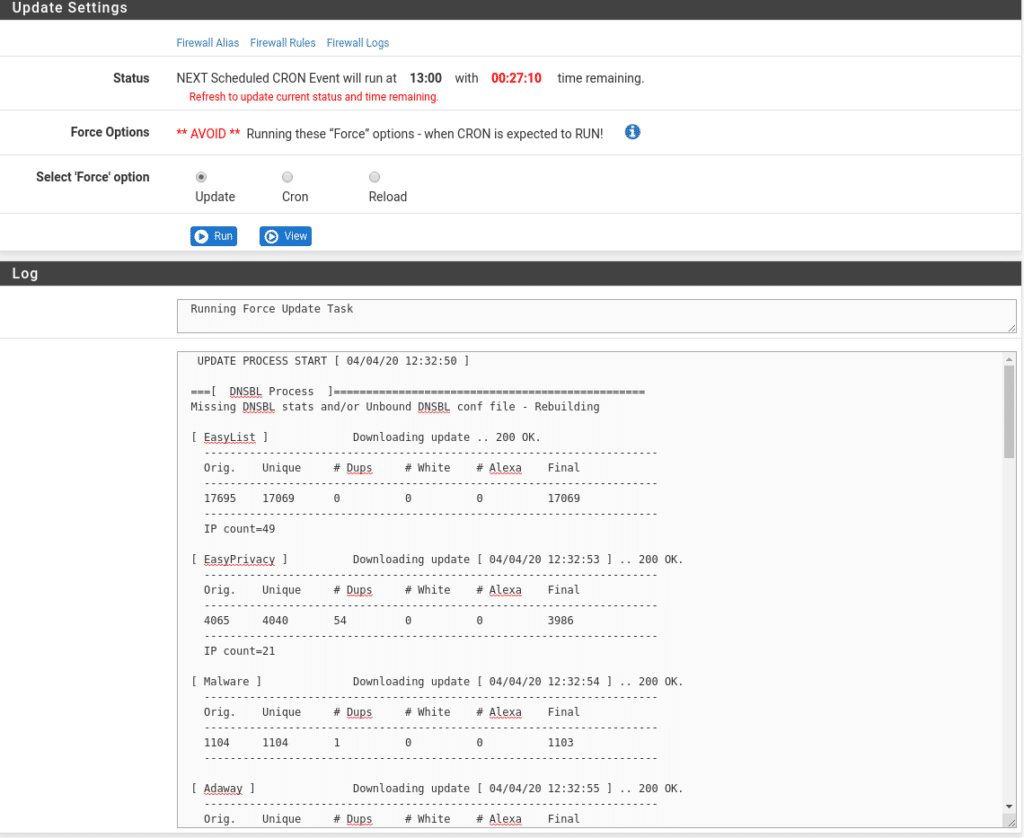
Now we force an update in Firewall/pfBlockerNG/Update and check that all our lists return a 200 OK and that the process finishes correctly, if any list fails check the url of that list or if it has been discontinued, this process should be reviewed at least once a month to know that we do not have discontinued lists like ransomwaretracker.
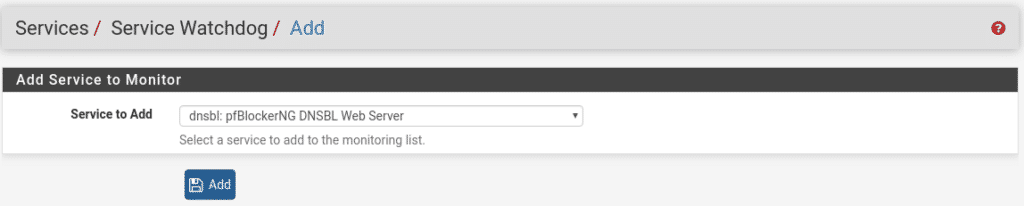
And finally we will go to Services/Service Watchdog and add pfBlockerNG, do this step whenever you add any service and even review the ones you have in case you are interested in monitoring any.
To check that it is working in this lab just activate the Level-1 rules, try to enter the firewall through the Wan where you will be blocked, launch the pfctl -d command from the console and in Firewall/pfBlockerNG/Alerts under Deny you will see the following
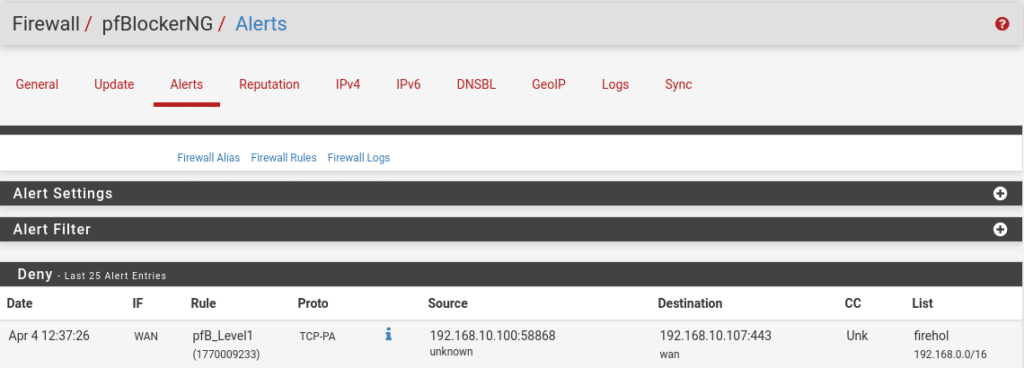
As we can see it is working perfectly blocking our ip according to the Level1 firehol list.
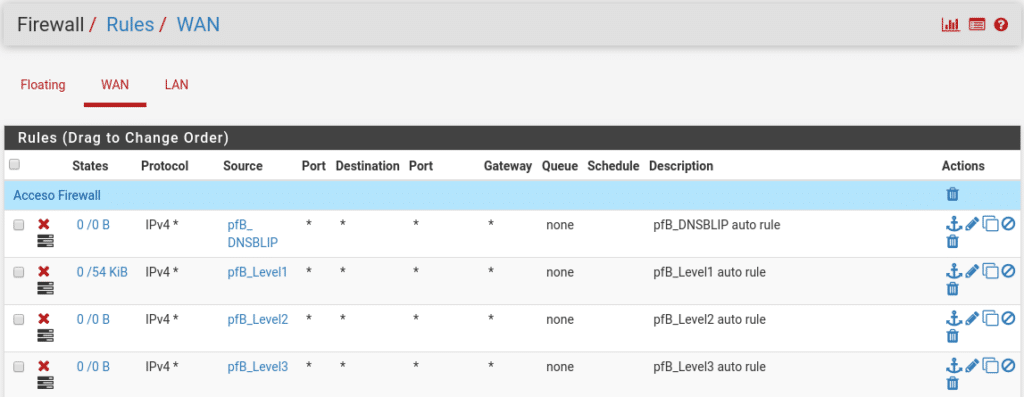
You will also notice in Firewall/Rules the rules that pfBlockerNG has added according to our categories
Well so far we have come in these posts about pfsense+suricata and pfBlockerNG, we could be writing months about pfsense, if you need a guide on any aspect or problem in pfsense, do not hesitate to write us.
Live life happily
TL.